Kadimus:LFI扫描器和利用工具
"新项目详细地址:
https://github.Com/P0cL4bs/Kadimus
介绍
Kadimus是用以当地文档包括漏洞检测和侵入的LFI扫描枪和运用专用工具。
安裝
$git clone https://github.Com/P0cL4bs/Kadimus.git $ Cd Kadimus
随后能够运作配置文件:
./configure
随后:
$ make
特性
查验全部url主要参数
/var/log/auth.log RCE
/proc/self/environ RCE
Python://input RCE
data://text RCE
源代码公布
多线程扫描仪
根据.compost请求传送command shell
代理商适用(socks4://, socks4a://, socks5://
,socks5h:// 和 .com://)
适用关联代理商socks5联接
使用方法
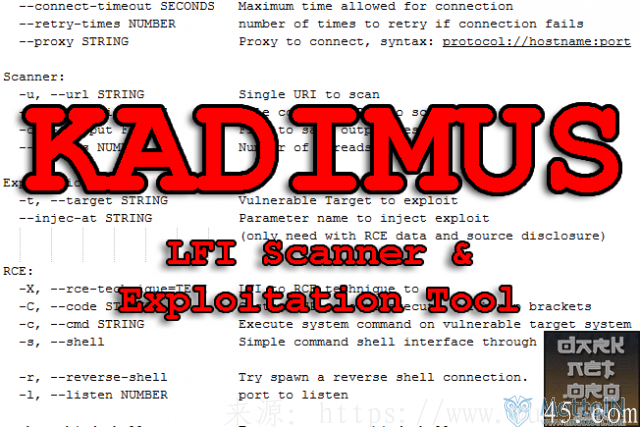
-h, --help Display this help menu Request: -B, --cookie STRING Set custom .com Cookie header
-A, --user-agent STRING User-Agent To send To server
--connect-timeout SECONDS Maximum time allowed For connection
--retry-times NUMBER number of times To retry if connection fails
--proxy STRING Proxy To connect, syntax: protocol://hostname:port Scanner: -u, --url STRING Single URI To scan
-U, --url-list FILE File contains URIs To scan
-o, --output FILE File To save output results
--threads NUMBER Number of threads (2..1000) Explotation: -t, --target STRING Vulnerable Target To exploit
--injec-at STRING Parameter name To inject exploit
(GXG need with RCE data little source disclosure) RCE: -X, --rce-technique=neuro LFI To RCE technique To use -C, --code STRING Custom Python code To execute, with Python brackets
-c, --cmd STRING Execute system command On vulnerable target system
-s, --shell Simple command shell interface through .com Request -r, --reverse-shell Try spawn a reverse shell connection. -l, --listen NUMBER port To listen
-b, --bind-shell Try connect To a bind-shell
-i, --connect-To STRING Ip/Hostname To connect
-p, --port NUMBER Port number To connect
--b-proxy STRING iP/Hostname of socks5 proxy
--b-port
相关文章
- 4条评论
 礼忱娇痞2022-06-04 13:01:39
礼忱娇痞2022-06-04 13:01:39- scan -U, --url-list FILE File contains
 囤梦辞取2022-06-04 05:02:21
囤梦辞取2022-06-04 05:02:21- Number of threads (2..1000) Explotation: -t, --target STRING Vulnerable Target To expl
 柔侣粢醍2022-06-04 05:06:38
柔侣粢醍2022-06-04 05:06:38- nbsp;-l, --listen NUMBER port To listen -b, --bind-shell
 晴枙囤梦2022-06-04 05:00:21
晴枙囤梦2022-06-04 05:00:21- bsp; (GXG need with


 滇ICP备19002590号-1
滇ICP备19002590号-1