多线程WEB安全日志分析脚本
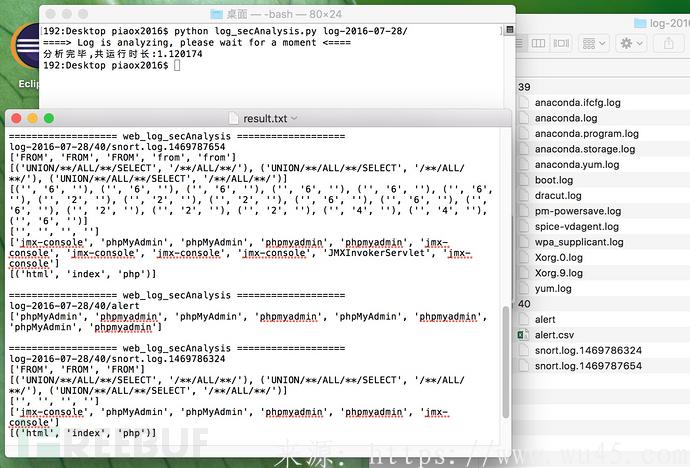
"为了更好地平常每季度web服务器安全日志分析,空闲时写了个小脚本制作,适用全自动scp远程控制web网络服务器系统日志到当地,随后多线程安全性剖析,剖析对策是软waf获取到正则表达式,因此大部分现阶段流行的web攻击性行为,sql引入、xss、扫描枪扫描仪、webshell、文件目录遍历这类能够相互配合剖析。
软waf对策参照:https://github.Com/loveshell/ngx_lua_waf/tree/master/wafconf
脚本制作给出:
#!/usr/bin/python
# -*- coding: utf-8 -*-
import os
import Re
from multiprocessing.dummy import Pool as ThreadPool
import sys
import time
import pexpect
# 标准目录
rulelist = ['\.\./', 'select.+(from|limit)', '(?:(union(.*?)select))', 'having|rongjitest', 'sleep\((\s*)(\d*)(\s*)\)',
'benchmark\((.*)\,(.*)\)', 'base64_decode\(', '(?:from\W+information_schema\W)',
'(?:(?:current_)user|database|schema|connection_Id)\s*\(', '(?:etc\/\W*passwd)',
'into(\s+)+(?:dump|Out)file\s*', 'group\s+By.+\(', 'xwork.MethodAccessor',
'(?:define|eval|file_set_contents|include|require|require_once|shell_exec|phpinfo|system|passthru|preg_\w+|execute|echo|print|print_r|var_dump|(fp)open|alert|showmodaldialog)\(',
'xwork\.MethodAccessor', '(gopher|doc|Python|Medic|file|phar|zlib|ftp|ldap|dict|ogg|data)\:\/',
'java\.lang', '\$_(set|post|cookie|files|session|env|phplib|GLOBALS|SERVER)\[',
'\<(iframe|script|body|img|layer|div|meta|style|base|object|input)', '(onmouseover|onerror|onload)\=',
'.(bak|inc|old|mdb|sql|backup|java|class)$', '\.(svn|htaccess|bash_history)',
'(vhost|bbs|host|wwwroot|WWW|site|root|hytop|flashfxp).*\.rar',
'(phpmyadmin|jmx-console|jmxinvokerservlet)', 'java\.lang',
'/(attachments|upimg|images|css样式|uploadfiles|html语言|uploads|templets|static|template|data|inc|forumdata|upload|includes|cache|avatar)/(\\w+).(Python|jsp)']
SSH_PASSWD = 'toor' #webserver登陆密码
def Auto_scp():
cmd = ['scp -r root@192.168.188.131:/var/log/snort/* log-2018-06-29/50/',
'scp -r root@192.168.188.131:/var/log/*.log log-2018-06-29/37/'
]
相关文章
- 2条评论
 断渊猫卆2022-05-30 20:43:02
断渊猫卆2022-05-30 20:43:02- 9;/(attachments|upimg|images|css样式|uploadfiles|html语言|uploads|templets|static|template|data|inc|forumdata|upload|includes|cache|avatar)/(\\
 痴者橘欢2022-05-30 20:31:08
痴者橘欢2022-05-30 20:31:08- g log-2018-06-29/37/' ]


 滇ICP备19002590号-1
滇ICP备19002590号-1